Amazon Web Services, often called AWS, gives people a truly wide set of ways to build things on the internet. It offers, you know, hundreds of fully featured ways to get things done, all from special computer centers spread across the entire globe. This large collection of tools means you can pretty much find something for nearly any need you have, from handling simple websites to running really complex device networks. In some respects, it's a big help for businesses and groups of all kinds looking to set up their digital presence, especially when it comes to connecting everyday objects to the internet.
When you have devices out in the world, perhaps sensors in a field or machines in a factory, getting to them directly can be a bit of a puzzle. These devices, part of what we call the Internet of Things, often need someone to check on them, update their programs, or figure out why they might not be working as expected. That's where a secure connection comes into play, making sure only the right people can reach these remote pieces of equipment. This kind of access is, you know, really important for keeping everything running smoothly and safely.
One clever way to get this secure access to your internet-connected gadgets, particularly those managed through AWS, involves creating a special kind of pathway. This pathway lets you talk to your devices as if they were right next to you, even if they are miles away. It's a method that helps keep your device operations private and protected from unwanted eyes. So, let's explore how this useful connection method works and why it might be just what you need for your connected things.
- Loretta Lynn Net Worth
- Bernard Hopkins Net Worth
- Hairstyle Evolution
- Dermabrasion Tattoo Removal
- Uranus Transit In 7th House
Table of Contents
- What is an AWS IoT SSH Tunnel?
- How Does AWS IoT SSH Tunnel Help Remote Devices?
- Setting Up Your AWS IoT SSH Tunnel - A Gentle Walkthrough
- Can AWS IoT SSH Tunnel Be Used for Troubleshooting?
- Keeping Things Safe - Security with AWS IoT SSH Tunnel
- Real-World Uses for AWS IoT SSH Tunnel
- Common Issues and Tips for AWS IoT SSH Tunnel
- Exploring the Broader AWS Ecosystem for Your AWS IoT SSH Tunnel
What is an AWS IoT SSH Tunnel?
When you think about connecting to a far-off device, say a smart meter in a remote building, you usually need a way to send commands and receive information. A regular connection might not be safe enough for sensitive operations. That's where the idea of an AWS IoT SSH tunnel comes in. It's basically a protected passageway, a bit like a secret tube, that allows you to establish a secure shell connection to your internet-connected things. This shell connection, or SSH, is a widely accepted way to get command-line access to computer systems, and in this case, to your devices that are out in the field.
The core idea is that your device, which is registered with AWS IoT Core, can open a secure line back to the AWS cloud. Then, you, from your own computer, can connect to that same secure line through AWS. This means your device doesn't need to have an open door to the entire internet, which could be risky. Instead, it only talks to AWS, and AWS acts as a go-between, allowing you to reach your device securely. It's a pretty neat trick for keeping things locked down, so to speak. You know, it really helps with device safety.
This whole setup uses various parts of the AWS cloud to make it work. It leans on the messaging capabilities of AWS IoT Core, which is the service that lets your devices talk to the cloud and to each other. It also involves other elements, like identity and access management, to make sure only authorized users can set up these tunnels. The overall goal is to give you a way to interact with your remote gadgets directly and safely, almost as if you were plugging a cable right into them. It's a very practical tool for managing a scattered collection of devices.
- Minty Drink Crossword Clue
- Daniel Jorgensen Owl City
- Ann Taylor Eva Pants
- Stelen Keith Covel Net Worth
- Films Like Bring It On
How Does AWS IoT SSH Tunnel Help Remote Devices?
Remote devices, whether they are small sensors or larger industrial machines, often operate in places where direct physical access is not easy or practical. Think about a weather station on a mountain, or a piece of equipment deep inside a factory that's hard to reach. Traditionally, if something went wrong or an update was needed, someone would have to travel to that location. This can be time-consuming and expensive, and honestly, sometimes it's just not possible. That's where an AWS IoT SSH tunnel offers a significant advantage.
By using this secure connection, you can send commands to your device, check its status, or even install new software without ever leaving your desk. It gives you the ability to troubleshoot problems from afar, which is a major benefit. For instance, if a device stops sending data, you could use the tunnel to log in, inspect its system logs, and perhaps restart a service. This kind of remote interaction means that you can react quickly to issues, keeping your device network running smoothly with less downtime. It's a very effective way to manage a fleet of devices that are spread out.
Moreover, this method helps with keeping devices current. Software updates are a regular part of maintaining any connected gadget, and an AWS IoT SSH tunnel provides a safe channel to deliver these updates. Instead of having to physically touch each device, you can push out changes over the secure tunnel. This is particularly useful for devices that might be running older software versions or that need a quick security patch. It really simplifies the task of keeping many devices up to date, which, you know, can be a big job otherwise.
Setting Up Your AWS IoT SSH Tunnel - A Gentle Walkthrough
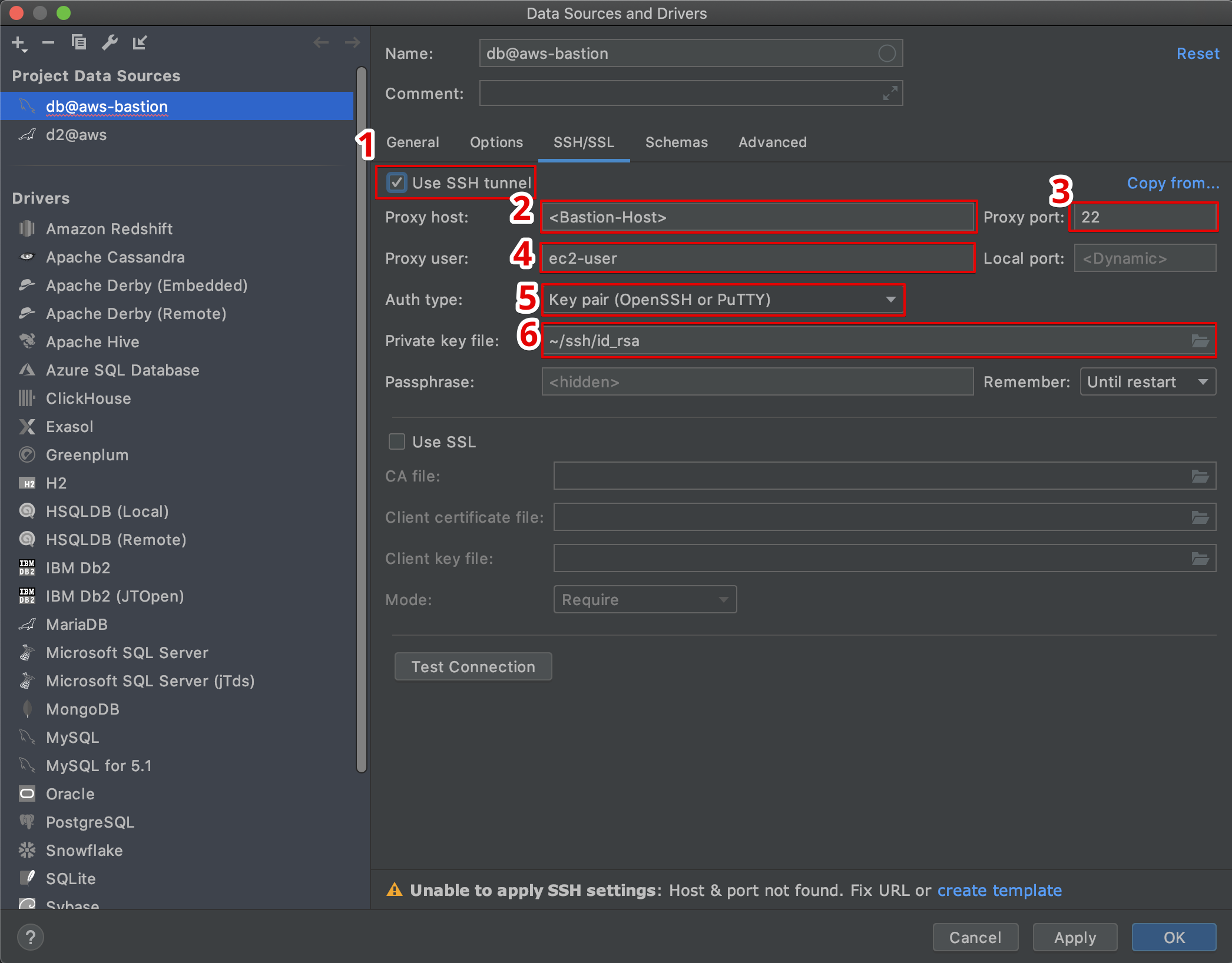
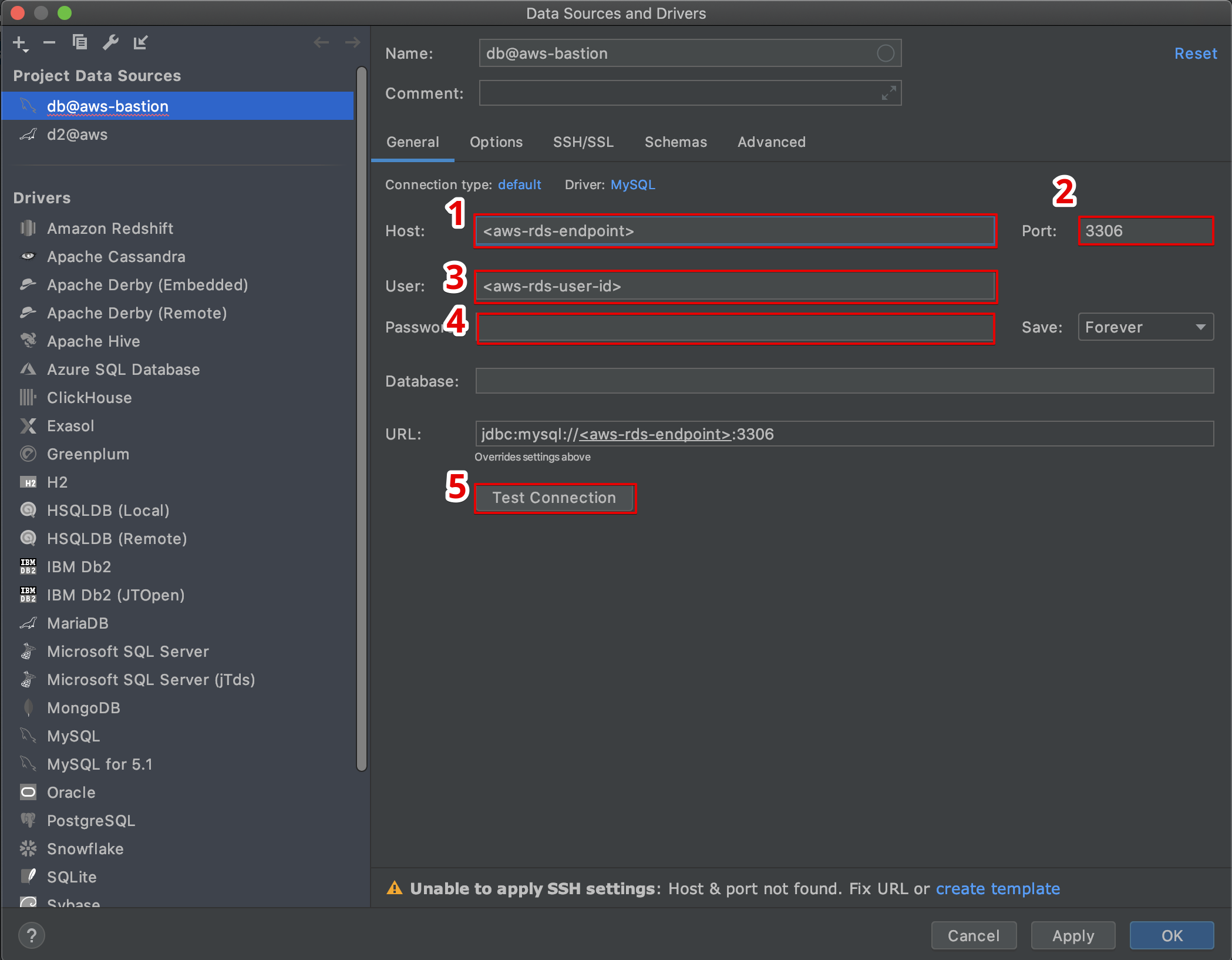
Getting an AWS IoT SSH tunnel ready for use involves a few steps, but it's not as difficult as it might seem at first glance. The process generally begins with making sure your device is properly set up and connected to AWS IoT Core. This means your device needs to have a unique identity and be able to communicate with the cloud service. Think of it like giving your device its own passport and a way to call home. There are, for example, guides available from AWS that help you learn the basic steps for connecting devices, which is a good place to start.
Next, you'll need to prepare your AWS account to allow for these secure connections. This often involves setting up certain permissions and roles within AWS Identity and Access Management (IAM). These permissions dictate who can create and use the tunnels, ensuring that only authorized individuals have access. It's about putting the right locks on the right doors, so to speak. You might also need to set up some network configurations, making sure that the data can flow freely but securely between your device, AWS, and your own computer. This part is, you know, pretty important for the whole system to function correctly.
Finally, you'll use a command-line tool or a special piece of software to initiate the tunnel connection from your computer. This tool tells AWS that you want to open a secure pathway to a specific device. AWS then works its magic, connecting you through its services to your device. Once the tunnel is open, you can then use standard SSH client software to connect to your device as if it were on your local network. It’s a bit like dialing a special number that connects you directly to the device, no matter where it is. This whole setup, you see, makes remote device management a lot more manageable.
Can AWS IoT SSH Tunnel Be Used for Troubleshooting?
Absolutely, an AWS IoT SSH tunnel is a very useful tool for figuring out problems with your devices. When a device isn't acting as it should, one of the first things you often need to do is get a closer look at what's happening on the device itself. This might mean checking system messages, looking at logs, or running diagnostic tools. If the device is far away, doing this directly is a big challenge. That's why the tunnel becomes so helpful.
With a secure tunnel in place, you can log into the device and examine its internal workings as if you were sitting right in front of it. You can see what programs are running, check how much memory is being used, or look for error messages that might explain the issue. This direct access is, you know, incredibly valuable for pinpointing the root cause of a problem quickly. It means you don't have to guess what's going on; you can actually see it.
For example, if your device is supposed to be sending data but isn't, you could use the AWS IoT SSH tunnel to connect and verify its network settings, or perhaps restart the software responsible for sending the information. This kind of hands-on investigation, even from a distance, saves a lot of time and effort. It helps keep your devices operational and reduces the need for someone to physically go out and check on them, which is, in some respects, a huge benefit for managing a large collection of internet-connected things.
Keeping Things Safe - Security with AWS IoT SSH Tunnel
When you're dealing with devices that are out in the world, especially those that might be collecting sensitive information or controlling important systems, security is a top concern. You want to make sure that only authorized people can get to them and that the information flowing back and forth is kept private. This is where the AWS IoT SSH tunnel truly shines, as it's built with a strong focus on protection. It uses established security methods to keep your device connections safe from unwanted attention.
The tunnel itself relies on standard SSH protocols, which are known for their ability to encrypt data. This means that any information passing through the tunnel is scrambled, making it unreadable to anyone who might try to intercept it. Furthermore, AWS uses its own security features, like identity verification and access controls, to make sure that only users with the right permissions can even open a tunnel to your devices. This layered approach to safety helps prevent unauthorized access and keeps your operations secure. It's a very thoughtful way to handle remote access.
Think of it this way: instead of leaving a door wide open for anyone to walk through, the AWS IoT SSH tunnel creates a locked, private hallway directly to your device. Only those with the correct digital keys and permissions can enter this hallway. This is a big step up from less secure methods, as it helps protect your devices from various online threats. So, when you use an AWS IoT SSH tunnel, you're not just getting remote access; you're getting remote access that is, you know, designed to be very secure from the ground up.
Real-World Uses for AWS IoT SSH Tunnel
The ability to securely reach remote devices has many practical applications across different types of businesses and situations. One common use for an AWS IoT SSH tunnel is for remote maintenance. Imagine a company that has vending machines spread across many cities. If a machine needs a software update or a quick fix, sending a technician to each one can be a logistical nightmare. With the tunnel, a technician can connect remotely, perform the necessary tasks, and get the machine back to serving customers quickly. This saves a lot of time and resources, too.
Another important use is for diagnostics and performance monitoring. Devices in the field can sometimes behave unexpectedly, and it's not always clear why. Using the tunnel, engineers can log into the device, collect real-time data, and monitor its performance. This helps them understand how the device is operating under actual conditions and identify any potential issues before they become major problems. For instance, if a sensor is giving odd readings, you could connect via the tunnel to check its calibration or software settings. This kind of proactive checking is, you know, really valuable for keeping systems running well.
The tunnel also proves useful for setting up and configuring new devices after they've been deployed. Sometimes, a device might need some final tweaks or a specific configuration once it's in its permanent location. Instead of having to physically connect to it with a cable, the AWS IoT SSH tunnel allows for this initial setup to be done remotely and securely. This makes the process of getting new devices online much smoother, especially when dealing with a large number of them. It's a very flexible tool for managing the entire life cycle of your connected things.
Common Issues and Tips for AWS IoT SSH Tunnel
While setting up and using an AWS IoT SSH tunnel is quite straightforward, people sometimes run into a few common snags. One frequent issue involves permissions. If the user or the device doesn't have the exact right set of permissions in AWS, the tunnel simply won't open. It's like trying to open a locked door without the correct key. A good tip here is to double-check your AWS Identity and Access Management (IAM) roles and policies, making sure they grant the necessary actions for establishing and maintaining the tunnel. You know, getting these permissions right is crucial.
Another point where things can get tricky is with network settings on the device itself. The device needs to be able to reach AWS IoT Core, and sometimes local firewalls or network configurations can prevent this communication. If your device can't talk to the AWS cloud, then a tunnel can't be established. A helpful suggestion is to verify your device's network connectivity and ensure that it can send and receive messages from AWS. Sometimes, it's just a matter of opening a specific port or allowing certain network traffic. It's a very common thing to check.
Finally, keeping track of the tunnel's status can sometimes be a bit of a challenge. Tunnels might close due to inactivity or network interruptions. If you're having trouble connecting, it's a good idea to check the tunnel's current state within the AWS console or using the AWS command-line tools. Sometimes, simply restarting the tunnel creation process can resolve the issue. Also, ensuring your SSH client software is up-to-date and correctly configured can prevent many headaches. These small checks can, in some respects, save you a lot of time when troubleshooting your AWS IoT SSH tunnel.
Exploring the Broader AWS Ecosystem for Your AWS IoT SSH Tunnel
The AWS IoT SSH tunnel doesn't exist in a vacuum; it's part of a much larger collection of tools and services that Amazon Web Services offers. This vast collection, which includes over two hundred fully featured services, provides a rich environment for building and managing nearly any kind of digital operation. When you think about getting started with AWS, you'll find plenty of ways to learn the basic ideas and begin putting things together. This foundational knowledge is, you know, really helpful when you're setting up something like an IoT tunnel.
For example, AWS provides a wide variety of computing power options, ways to store your information, and database systems. All of these are designed to give you good value for your money and work well. This includes a very complete set of artificial intelligence and data services, which can be used to make sense of the information your IoT devices collect. If you need to access a device that's running some kind of machine learning model, the tunnel gives you a secure way to do that. It’s a very interconnected system.
If you're looking to gain a better grasp of how cloud computing works and how AWS fits into that picture, there are many resources available. You can find answers to common questions and discover good ways to build things on AWS. There are, for instance, hundreds of free online courses put together by experts at AWS that can help you learn. These learning opportunities can help you better understand how services, including those related to your AWS IoT SSH tunnel, fit together and how to use them effectively. It really helps to see the whole picture.
Related Resources:

Detail Author:
- Name : Phyllis Kub
- Username : welch.amir
- Email : paul72@hotmail.com
- Birthdate : 2000-10-25
- Address : 29900 Bartoletti Grove Apt. 820 Watershaven, SC 94952
- Phone : 930-399-3266
- Company : Leannon, Haag and Douglas
- Job : Online Marketing Analyst
- Bio : Voluptatem nemo possimus temporibus dolores sit et. Et nobis numquam sed et. Quia voluptatem voluptatum aliquid explicabo quis.
Socials
tiktok:
- url : https://tiktok.com/@garnett6178
- username : garnett6178
- bio : Vel quo repellat totam ut. Tenetur accusamus nulla quaerat non eligendi.
- followers : 2863
- following : 976
facebook:
- url : https://facebook.com/garnett_streich
- username : garnett_streich
- bio : Exercitationem repellat rerum et quia iusto.
- followers : 4306
- following : 1561