Connecting various gadgets and contraptions to the internet can feel a bit like orchestrating a very large, very scattered band. Each instrument, or device, needs its own way to communicate, and keeping them all in tune and secure is a pretty big job. Luckily, there are ways to make this whole process much less of a headache, especially when you're thinking about how your smart things talk to the big wide web.
You see, when we talk about things like remote access for your internet-connected devices, we're really talking about making sure they can be reached and managed, no matter where they are. This is where a helpful service from Amazon Web Services, often called AWS IoT Core, steps in. It's like a central hub, a meeting point for all your devices, allowing them to send and receive information in a very organized fashion, which is quite useful, you know?
And when it comes to getting a closer look at what your devices are doing, or maybe fixing something on them from afar, a familiar method called SSH often comes to mind. It’s a way to securely get into a device and type commands, almost like you’re sitting right in front of it. Bringing this secure access method together with a powerful cloud platform for connected devices, like AWS IoT Core, opens up some very interesting possibilities for managing your gadgets, so it's a topic worth exploring.
- Live And Breathe Crossword
- Winslow Cool Breeze On The Underground Download
- Jimmy Buffett Tequila
- Live And Breathe Crossword Clue
- Patti Stanger Parents
Table of Contents
- What is AWS IoT Core and Why Does it Matter?
- Getting Devices Talking - The Basics of AWS IoT Core
- Securing Your Connections - Is AWS IoT Core SSH Safe?
- Setting Up Remote Access with AWS IoT Core SSH
- Common Hurdles with AWS IoT Core SSH
- What's Next for Your Connected Things?
What is AWS IoT Core and Why Does it Matter?
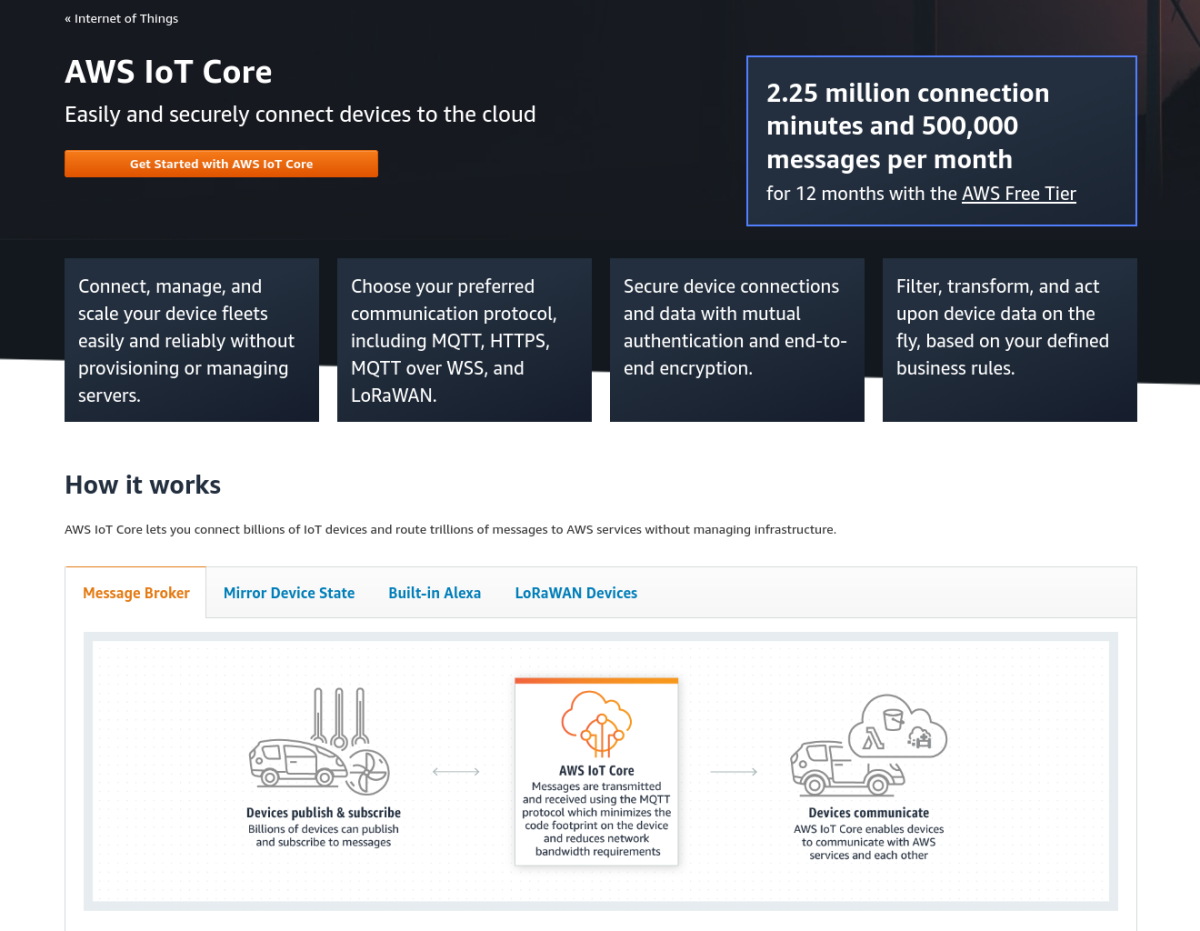
So, what exactly is this AWS IoT Core thing, and why should anyone care about it? Well, imagine you have a whole bunch of smart devices – maybe sensors collecting weather information, or little cameras watching over a space, or even machines on a factory floor doing their work. Each of these devices needs a way to send its information somewhere useful, and sometimes, they need to receive instructions back. This is where AWS IoT Core comes into play. It's like a central post office for all your connected gadgets, allowing them to send messages back and forth in a very orderly and secure way. It handles a lot of the trickier parts of connecting millions of devices, making sure their messages get to the right place without too much fuss. It's a pretty big deal for anyone building things that talk to the internet, you know, because it makes that communication reliable.
This service is a part of a much bigger collection of tools provided by Amazon Web Services, which is a very widely used cloud platform. This platform offers many different ways to handle computing tasks, store vast amounts of information, manage data, and even do clever things with machine learning. AWS IoT Core is one of those specialized tools, specifically built for the needs of internet-connected items. It helps you manage the connections, keep things secure, and process the constant stream of information coming from your devices. It's a rather essential piece of the puzzle for anyone wanting to build a system where many devices work together, perhaps even millions of them, which is quite impressive.
How does AWS IoT Core SSH fit in?
Now, when we talk about getting into those devices for maintenance or a quick check, that’s where the idea of AWS IoT Core SSH starts to make sense. Normally, if you wanted to access a device remotely using SSH, you'd need that device to have a direct, open pathway on the internet, which isn't always the safest or most practical thing, especially for small, resource-limited gadgets. AWS IoT Core helps bridge this gap. It provides a secure way for your devices to communicate with the cloud, and within that framework, there are clever ways to enable remote access like SSH without exposing your devices directly to the wider internet. It's a bit like having a secure, private tunnel from your computer to your device, with AWS IoT Core acting as the secure gateway for that tunnel, which is quite convenient, honestly.
- Step Dad Step Daughter Wedding Songs
- Stelen Keith Covel Net Worth
- Best Dramas With A Twist
- How To Write Obituary For Dad
- Best And Worst Careers For Virgos
Getting Devices Talking - The Basics of AWS IoT Core
Getting your devices to actually communicate with AWS IoT Core involves a few fundamental steps. First, each device needs to be identified within the system. This is done by giving it a unique identity, almost like a name tag, and setting up credentials, which are like a special key and lock that only your device can use to talk to the service. This ensures that only authorized devices can send data or receive commands. It’s a pretty important first step, making sure everything is properly recognized and secure from the start, so you're not just letting any device connect, you know?
Once a device has its identity and credentials, it can begin sending its information. This data usually goes through a messaging system within AWS IoT Core, which can handle a very large number of messages coming in from many different devices all at once. Think of it like a very busy switchboard that directs all the incoming calls to the right place. This system also allows you to send commands back to your devices, like telling a smart light to turn on or off. It’s a basic, yet powerful, way to keep your connected things working in sync with your overall system, and it works quite well for managing lots of devices.
Preparing for AWS IoT Core SSH Access
Before you can even think about using AWS IoT Core SSH to get into your devices, there are some preparations you need to make. Your device itself needs to be set up to accept SSH connections. This means having the right software installed on it, and usually, setting up a way for it to handle SSH keys instead of passwords, which is a much safer approach. You'll also need to make sure your device has a way to talk to AWS IoT Core in the first place, which involves setting up its identity and permissions, as mentioned earlier. It’s like getting all your ducks in a row before you can start the actual work, so everything runs smoothly, you know, just a little bit of planning goes a long way.
Beyond the device, you'll also need to consider the network setup. While AWS IoT Core helps avoid direct exposure, you still need to ensure your device can reach the AWS IoT Core endpoints. This usually involves making sure firewalls or network settings on the device or its local network allow outgoing connections to the necessary AWS services. It's a bit like making sure the road to the post office is clear before you send your mail. Getting these preliminary steps right is pretty important for a reliable AWS IoT Core SSH connection later on, and it really helps avoid headaches down the line.
Securing Your Connections - Is AWS IoT Core SSH Safe?
When you're dealing with remote access to devices, especially ones out in the real world, security is probably the first thing that comes to mind. Is using something like AWS IoT Core SSH truly safe? The good news is that SSH itself is a very secure protocol when used correctly, and AWS IoT Core is built with security as a core principle. The way it generally works is by creating a secure, temporary tunnel between your management computer and the device, mediated by the AWS cloud. This means your device isn't just sitting there with an open SSH port for anyone on the internet to try and connect to, which is a much safer arrangement, you know? It's like having a bouncer at the door, only letting in authorized visitors.
However, just because the tools are secure doesn't mean you can ignore your own part in keeping things safe. The safety of your AWS IoT Core SSH setup largely depends on how you manage your keys, your device identities, and the permissions you grant. Using strong, unique SSH keys, rotating them regularly, and making sure only the right people or systems have access to them are all very important. It’s a bit like having a very strong lock on your door, but also making sure you don't leave the key under the doormat. So, while the underlying system is quite robust, your practices play a big role in its overall safety, which is pretty much true for any security setup.
Best practices for AWS IoT Core SSH security
To keep your AWS IoT Core SSH connections as safe as possible, there are several things you should really focus on. First, always use SSH key pairs instead of passwords. Keys are much harder to guess or crack. Second, make sure your private keys are stored in a very secure place, perhaps even encrypted, and that only authorized personnel can access them. Third, limit the permissions granted to your devices and the users who can initiate these SSH sessions. Give them only the bare minimum access they need to do their job, nothing more. This is often called the principle of least privilege, and it's a pretty good rule to live by for security, honestly.
Another important practice for AWS IoT Core SSH security involves monitoring. Keep an eye on who is connecting to your devices and when. AWS provides tools that let you log and audit activity, which can help you spot anything unusual. Also, consider setting up automatic alerts for suspicious connection attempts. Finally, keep your device software updated. Patches often fix security weaknesses, so keeping your device's operating system and applications current is a simple yet very effective way to reduce risks. These steps, taken together, make your remote access setup much more resilient against unwanted intrusions, which is something you definitely want.
Setting Up Remote Access with AWS IoT Core SSH
Setting up remote access using AWS IoT Core SSH involves a few distinct stages. First, you need to configure your devices to act as targets for these remote sessions. This means making sure they have an SSH server running and are ready to accept connections, but importantly, not directly from the open internet. Instead, they'll be listening for instructions that come through the secure channels provided by AWS IoT Core. This setup typically involves installing certain agents or software on the device that can communicate with the AWS IoT Core service, acting as the intermediary for your SSH commands. It’s a bit like preparing a special entrance for a delivery, rather than leaving the main door wide open, which is a rather smart approach.
Next, you'll need to define the rules and permissions within AWS that allow specific users or systems to initiate these remote sessions to your devices. This often involves setting up policies that specify which devices can be accessed and by whom. AWS provides various ways to manage these permissions, ensuring that only authorized individuals can establish an AWS IoT Core SSH session. This control layer is very important for maintaining security and making sure that remote access is only used for legitimate purposes. It’s about putting the right gatekeepers in place, so to speak, and it’s a pretty standard security measure.
Step-by-step for AWS IoT Core SSH
Let's walk through a simplified step-by-step idea for getting AWS IoT Core SSH working. First, make sure your device has an SSH server ready. This is usually a standard part of Linux-based systems, but you'll need to confirm it's active. Second, install the necessary AWS IoT Device Client or similar agent on your device. This software helps your device communicate with AWS IoT Core and handle the secure tunneling process. Third, register your device with AWS IoT Core, giving it a unique name and attaching security certificates so it can prove its identity. This is a pretty fundamental step for any device connecting to the service, you know?
Fourth, you'll need to set up a secure tunneling service within AWS, often using something like AWS IoT Secure Tunneling. This service creates the secure pathway between your local machine and your remote device, mediated by AWS IoT Core. You'll generate a tunnel, and the device client will connect to its end of the tunnel. Fifth, from your local machine, you'll use a local proxy or a similar tool to connect to your end of the tunnel. This local proxy then forwards your standard SSH client commands through the secure tunnel to your device. Finally, you can use your regular SSH client, like PuTTY or the `ssh` command, to connect to your device through that local proxy. It sounds like a few steps, but it provides a very secure way to get into your remote gadgets, which is pretty neat.
Common Hurdles with AWS IoT Core SSH
Even with all the benefits, getting AWS IoT Core SSH to work perfectly can sometimes present a few common challenges. One frequent issue is related to permissions. If your device doesn't have the correct AWS Identity and Access Management (IAM) permissions to connect to the secure tunneling service, or if your user doesn't have permission to create and manage tunnels, you'll run into roadblocks. It's a bit like trying to open a locked door without the right key; nothing will happen until you get the permissions sorted out. Checking your IAM policies is often the first place to look when things aren't connecting as expected, which is a pretty common troubleshooting step.
Another hurdle can be network configuration on the device side. Even though AWS IoT Core helps with remote access, your device still needs to be able to make outbound connections to the AWS endpoints for the tunneling service. If there are firewalls, proxies, or strict network rules on the device's local network that block these connections, the tunnel won't establish. It’s a bit like trying to make a phone call, but your phone isn't connected to the network. Making sure your device can reach the necessary AWS services over the internet is very important for the whole setup to function correctly, and it's a point that sometimes gets overlooked, you know?
Troubleshooting AWS IoT Core SSH issues
When you hit a snag with AWS IoT Core SSH, there are some pretty standard troubleshooting steps you can take. First, check the logs. Both on your device and within the AWS console, there are logs that can give you clues about why a connection failed. Look for error messages related to authentication, permissions, or network connectivity. These messages are often very helpful in pointing you in the right direction. Second, verify your credentials and keys. Make sure the SSH keys you're using locally match what's expected on the device, and that your device's AWS certificates are still valid and correctly configured. It's a bit like double-checking your address before sending a letter, just to be sure.
Third, confirm network reachability. From your device, try to ping or make a simple connection to the AWS IoT Core endpoints to ensure it can communicate with the service. If it can't, then you'll need to investigate local network settings, firewalls, or proxy configurations. Fourth, review your AWS IoT Core SSH policies and permissions. Ensure that the specific device is allowed to create tunnels and that the user initiating the connection has the necessary permissions. Sometimes, a small typo or an overlooked permission setting can cause a lot of frustration. Taking a systematic approach to these checks can save you a lot of time and help you get your remote access working as intended, which is quite satisfying.
What's Next for Your Connected Things?
Once you've got your devices happily communicating and you can even remotely access them using AWS IoT Core SSH, what's the next step for your connected gadgets? Well, having this kind of reliable and secure access opens up many possibilities. You can start thinking about more advanced ways to manage your devices, perhaps automating software updates or pushing new configurations to them from a central location. This kind of remote capability is a pretty big deal for keeping your fleet of devices healthy and up-to-date without needing to physically touch each one. It really helps with maintaining a large number of deployed items, which is a significant benefit, you know?
Beyond basic maintenance, this reliable connection also allows for more sophisticated data collection and analysis. With your devices consistently sending information to AWS IoT Core, you can then use other AWS services to store, process, and even visualize that data. This could mean building dashboards to see the status of all your devices at a glance, or setting up alerts for unusual activity. It’s about turning raw data into useful insights, which can help you make better decisions about your operations or even create new services. The ability to connect and manage your devices securely is really just the beginning of what you can build with these cloud tools, and it’s a very exciting area to explore.
Future possibilities with AWS IoT Core SSH
Looking ahead, the use of AWS IoT Core SSH and similar remote management capabilities is only going to become more important as more and more things get connected to the internet. Imagine a world where you can diagnose an issue on a smart appliance in someone's home without sending a technician, or update the software on a remote sensor array in a distant field with just a few clicks. These kinds of scenarios become much more practical when you have a secure, scalable way to reach and interact with your devices. It's a pretty powerful concept, allowing for greater efficiency and responsiveness in managing distributed systems, which is something many businesses and organizations are looking for.
Furthermore, as the AWS cloud platform continues to grow and offer new services, the ways in which AWS IoT Core SSH can be integrated will also expand. We might see even more streamlined ways to initiate sessions, or more sophisticated tools for automating remote tasks. The idea is to make device management as simple and secure as possible, allowing people to focus on what their devices are *doing* rather than how to *reach* them. It's a rather promising outlook for anyone working with connected technology, as it makes the whole process much more manageable and opens doors to new applications, which is quite encouraging.
Related Resources:


Detail Author:
- Name : Nigel Mitchell
- Username : jamar02
- Email : jacques10@lesch.biz
- Birthdate : 2004-05-02
- Address : 91054 Breitenberg Mountain Suite 975 Port Alanis, IL 55117
- Phone : +1.504.770.4967
- Company : Johnson Ltd
- Job : Plating Operator
- Bio : Eos dolores velit rerum libero eos quisquam. Blanditiis fuga et amet. Ipsum recusandae officiis natus velit est reprehenderit et. Eveniet voluptatibus ex aut illum.
Socials
tiktok:
- url : https://tiktok.com/@emilia_wiegand
- username : emilia_wiegand
- bio : Assumenda dolores at impedit eius sint neque accusantium expedita.
- followers : 4491
- following : 816
twitter:
- url : https://twitter.com/emilia_wiegand
- username : emilia_wiegand
- bio : Et eos cumque non est et est saepe. Ad at nesciunt accusantium voluptas autem facilis asperiores. Soluta at quo consequatur perspiciatis eligendi iure ipsum.
- followers : 6885
- following : 910
instagram:
- url : https://instagram.com/wiegande
- username : wiegande
- bio : Nihil et ipsam sed vitae nihil aperiam. Sit dolorum rem totam id nam.
- followers : 6515
- following : 2732